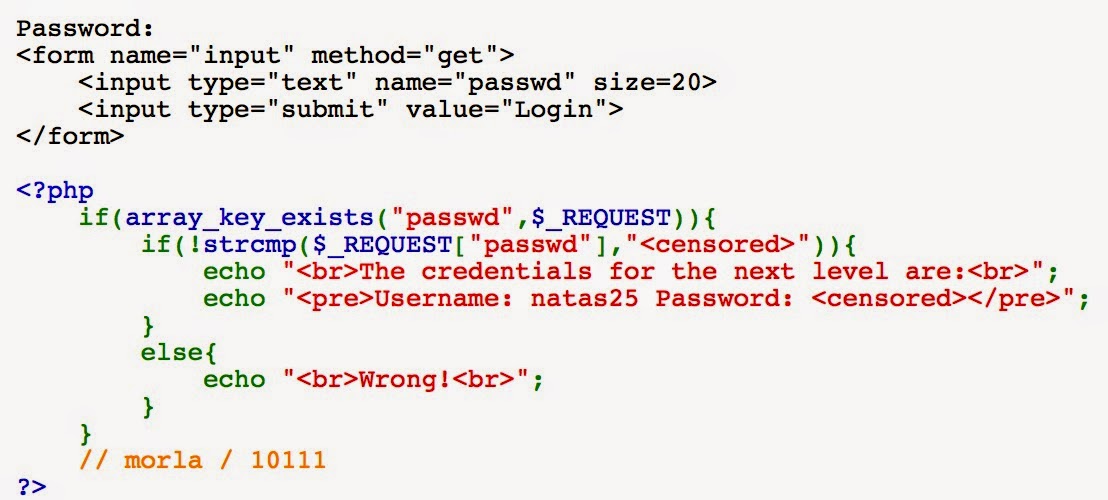
Natas 24 looks a lot like the last level -- a password login page:
Looking at the code, it looks pretty short again too!
Because the code is so short, it seems like whatever the vulnerability is will have to be within the strcmp() call.
We can guess that the probably aren't expecting us to brute-force the keyspace (the size field of the input form above is 20!), but there's got to be something else...
After trying a few things unsuccessfully and googling "strcmp php vulnerability", I came across a page that went into some interesting details about how strcmp() may return 0 in cases where it's unable to do the comparison (for example, if one of the objects is an Array and the other is an integer).
This got me thinking, how can I set passwd to an array?
I tried entering Array() into the field, but that didn't seem to work.
Eventually, I realized that I could change the type in the GET request itself:
That seems to work -- the comparison fails to evaluate correctly, and we get the natas25 passcode!


No comments:
Post a Comment