Natas 20 looks different from 18 & 19 and only prompts for a name:
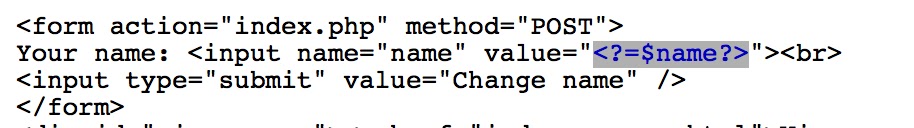
Taking a quick look at the source code (which is a bit longer than the previous challenges), it looks like it uses the name you give it in the page and associates this name to you using a session cookie.
By adding "?debug=true" on to the end of the URL, you can have it print out some additional debugging information, which might be useful later:
Interestingly, it's immediately clear that the welcome page is vulnerable to XSS:
But, after playing around with this for a while, it seemed like that wasn't going to get me anywhere.
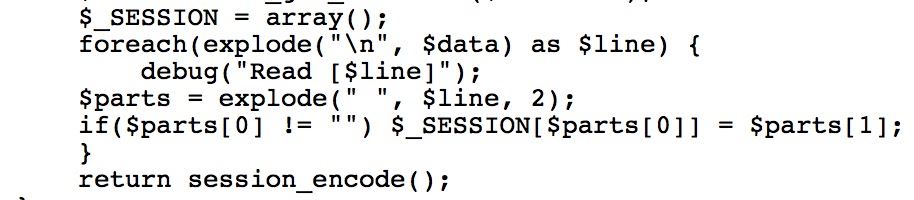
Looking through the code again, it looks like the parsing and setting of the session values is done in an interesting way:
This opens some doors -- if we can write arbitrary data to the file that's being read, what's to stop us from adding a newline character somewhere in there to have the reader interpret our single key-value pair as multiple?
Sending the following request twice does just that (%0A is url-encoded newline):
On the second response (the first one was just for writing to the session file), we get the password!




No comments:
Post a Comment