This is the 8th challenge from FireEye's 2015 "FLARE On" challenge (http://flare-on.com/)
Solution:
The 8th challenge was the stego one. Running the initial EXE file doesn't give too much info...
And opening it up in IDA shows there's really not much going on:
Looking through the data embedded in the file, it looks like there is some kind of structured data, however. Possibly Base64:
After using a hex editor to cut out the non-base64 data, I wrote a quick python script to translate the data to un-base64'd form.
This looks good -- Opening the written file in Notepad++ shows it has as PNG header!
Let's see what it looks like:
From here, I tried taking a look at it with StegSolve:
You can see something may be up when you look at the data planes on a per-bit level. Here's the 7th bit in the red plane:
Here are the 0th bits in each of the RGB planes. See the black bar at the top?
It makes sense that there may be some data hidden in there as the 0th bit would affect the picture the least and could easily be used for hiding some additional data.
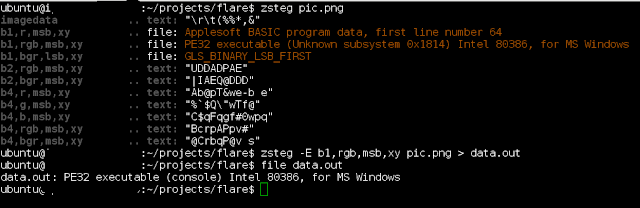
From here, I pulled it apart with "zsteg", which immediately detected a PE32 executable file and extracted it easily:
Running this EXE file gives you the email for the next level!








No comments:
Post a Comment