About:
This is the 1st challenge from FireEye's "FLARE On" challenge (http://flare-on.com/)
Solution:
$ file ./Challenge1.exe
./Challenge1.exe: PE32 executable for MS Windows (GUI) Intel 80386 32-bit Mono/.Net assembly
After running file on the binary and seeing it was a Windows executable written in .NET, I ran it in a Windows VM and was greeted by Bob Ross with a nice painting:
Hitting the DECODE! button makes both the picture and text change:
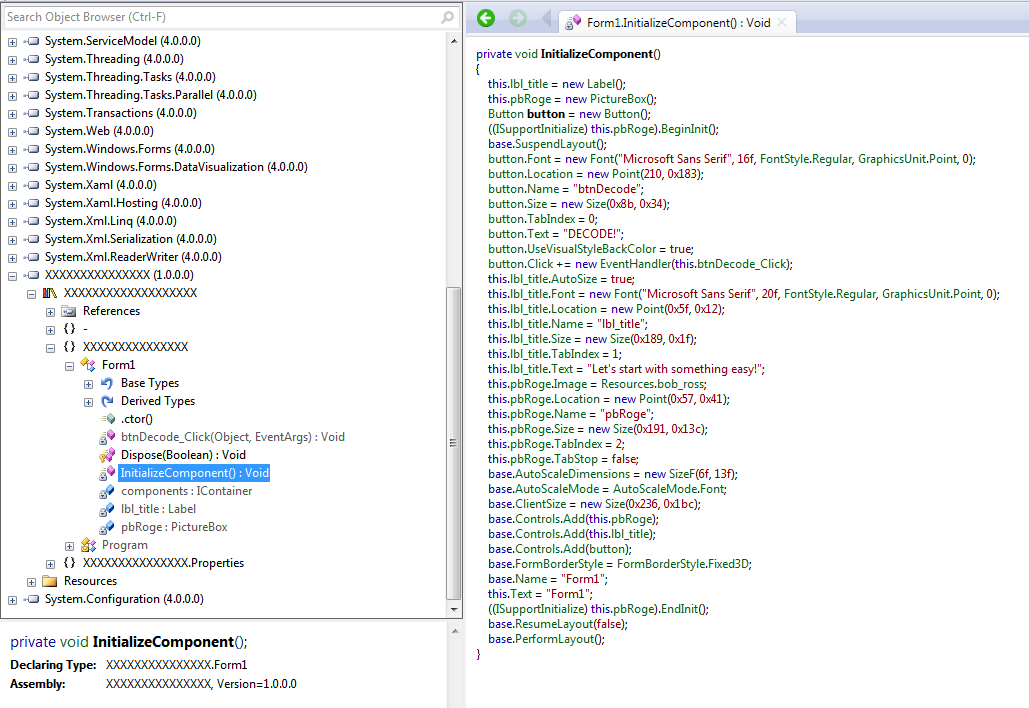
At this point, I opened up the trial version of Red Gate's .NET Reflector and started going through the decompiled code. The first thing that sticks out is the XXXXXXXXXXX object:
Looking through InitializeComponent(), it looks like this is where the main functionality is implemented.
You can see that btnDecode_Click() is used to handle the click event, so whatever it is, it's probably relevant:
It looks like some bit-fiddling of the dat_secret resource.
I took the dat_secret.encode object and wrote a quick python script to walk through the operations in btnDecode_Click():
#!/usr/bin/env python3
#
secret = "\xA1\xB5\x44\x84\x14\xE4\xA1\xB5\xD4\x70\xB4\x91\xB4\x70\xD4\x91\xE4\xC4\x96\xF4\x54\x84\xB5\xC4\x40\x64\x74\x70\xA4\x64\x44"
str1 = str2 = str3 = ""
for i in range(len(secret)):
num2 = ord(secret[i])
str1 += chr(((num2 >> 4) | ((num2 << 4) & 240)) ^ 0x29)
str1 += "\0"
for i in range(len(secret)):
str2 += str1[i + 1] + str1[i]
for i in range(len(str2)):
ch1 = str2[i]
str3 += chr(ord(str2[i])^0x66)
print(secret, str1, str2, str3, sep='\n')
When you run this, you get the following output:
$ python3 flare-01.py
¡µD„䡵Ôp´‘´pÔ‘äÄ–ôT„µÄ@dtp¤dD
3rmahg3rd.b0b.d0ge@flare-on.com
r3mramhagh3gr3dr.db.0bb0.bd.0dg0eg@ef@lfalraer-eo-no.nc.ocmom
U
UUHHVVHHVV&&
K K H
f
Looks like one of the intermediate strings (str1) is the target email address!




No comments:
Post a Comment